SOC 2 Compliance unlocks opportunities for small to medium-sized companies, allowing them to serve larger organizations with confidence.
Businesses are increasingly seeking cost-effective solutions by outsourcing critical functions, not only for cost management but also to relieve in-house staff, allowing them to concentrate on more significant projects. However, the shift of business functions and data to third-party SaaS or cloud providers introduces risks like data theft, extortion, and potential liability in case of a breach. The challenge is to safeguard reputation, integrity, and customer data security while enjoying the advantages of outsourcing.
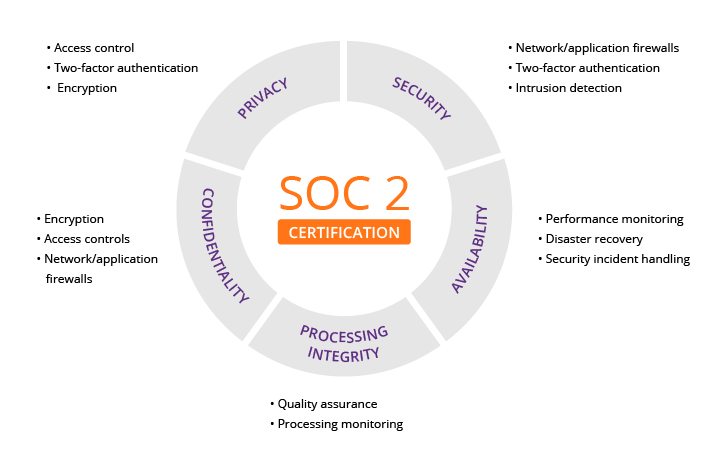
The SOC 2 audit plays a crucial role in providing assurance to businesses utilizing cloud or SaaS services. It is a compliance standard that assesses the policies and processes implemented by service organizations to safeguard client data throughout its transmission, storage, and management in the cloud. The audit ensures the presence of controls that guarantee system and data availability. Achieving SOC 2 compliance signifies that service organizations meet a heightened level of trust criteria.